3. SuperScan
 [youtube]http://www.youtube.com/watch?v=EwWmgixrZ1Y[/youtube]
[youtube]http://www.youtube.com/watch?v=EwWmgixrZ1Y[/youtube]
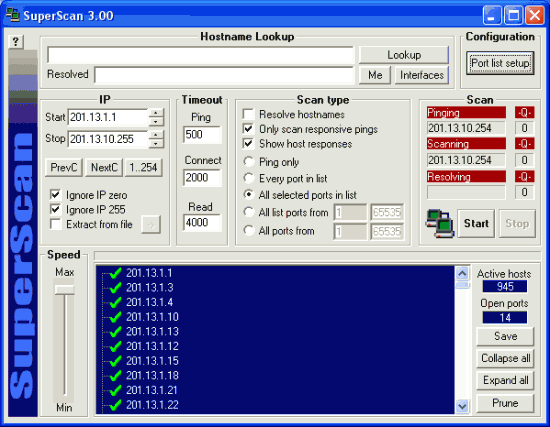
SuperScan is a free connect-based port scanning software designed to detect open TCP and UDP ports on a target computer, determine which services are running on those ports, and run queries such as whois, ping, ICMP traceroute, and Hostname lookups[1].
Superscan 4, which is a completely-rewritten update to the other Superscan, features windows enumeration, which can list a variety of important information dealing with Microsoft Windows such as:
a. NetBIOS information
b. User and Group Accounts
c. Network shares
d. Trusted Domains
e. Services – which are either running or stopped
Superscan is a tool used by both system administrators, crackers and script kiddies to evaluate a computer’s security. System administrators can use it to test for possible unauthorized open ports on their computer networks, whereas crackers use it to scan for a potentially insecure port in order to gain illegal access to a system.
2. John The Ripper
[youtube]http://www.youtube.com/watch?v=3YyscD_tADk[/youtube]
John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. Besides several crypt(3) password hash types most commonly found on various Unix flavors, supported out of the box are Kerberos AFS and Windows NT/2000/XP/2003 LM hashes, plus several more with contributed patches.
1. Nmap
Nmap (Network Mapper) is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are avalable for Linux, Windows, and Mac OS X.
In addition to the classic command-line Nmap executable, the Nmap suite includes an advanced GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
Nmap was named “Security Product of the Year” by Linux Journal, Info World, LinuxQuestions.Org, and Codetalker Digest. It was even featured in eight movies, including The Matrix Reloaded, Die Hard 4, and The Bourne Ultimatum.