The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Crackers had not yet had time to latch on to the new technology and wireless was not commonly found in the work place. However, there are a great number of security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Cracking methods have become much more sophisticated and innovative with wireless. Cracking has also become much easier and more accessible with easy-to-use Windows or Linux-based tools being made available on the web at no charge.
1. Data Interception:

It is generally understandable by everyone that data sent over Wi-Fi can be confined by eavesdroppers easily, within a few hundred feet; even farther with directional antennas. Fortunately, all Wifi Certified products supports AES-CCMP data encryption and integrity. Unfortunately, there are still legacy products that only speak TKIP, and many WLANs are configured to accept both AES and TKIP. But TKIP is vulnerable to message integrity check (MIC) attacks that allow a limited set of spoofed frames to be injected – for example, ARP. Although resulting risks are modest, the writing is on the wall: The time has come to retire TKIP and require AES-CCMP.
2. Denial of Service:
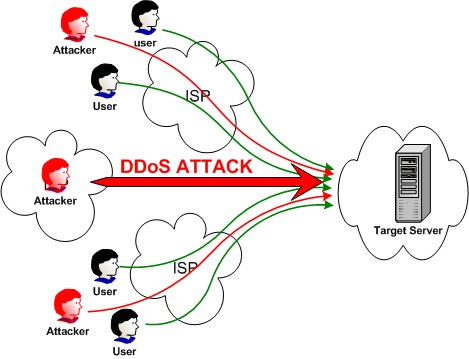
A “denial-of-service” attack is characterized by an explicit attempt by attackers to prevent legitimate users of a service from using that service. Examples include
– attempts to “flood” a network, thereby preventing legitimate network traffic
– attempts to disrupt connections between two machines, thereby preventing access to a service
– attempts to prevent a particular individual from accessing a service
– attempts to disrupt service to a specific system or person
WLANs are intrinsically defenseless to DoS. Everyone shares the same unlicensed frequencies, making competition expected in populated areas. The good news: As enterprise WLANs migrate to 802.11n, they can use channels in the larger, less-crowded 5 GHz band, reducing “accidental DoS.” Moreover, contemporary access points (APs) can auto-adjust channels to circumvent interference. But that still leaves DoS attacks: Phony messages sent to disconnect users, consume AP resources, and keep channels busy. To neutralize common DoS attack methods like Deauth Floods, look for newer products that support 802.11w management frame protection.
3. Rogue APs:
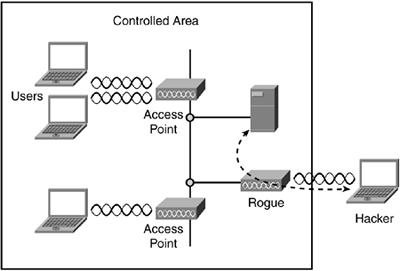
Business network penetration by unknown, unauthorized APs has long been a top worry. Fortunately, most enterprise WLANs now use legitimate APs to scan channels for possible rogues in their spare time. Unfortunately, verifying “true rogues” by tracing their wired network connectivity is a skill that ordinary WLAN gear has yet to perfect. Without accurate classification, automated rogue blocking is a risky proposition. To not just detect, but effectively mitigate rogue APs, deploy a Wireless IPS that can reliably differentiate between harmless neighbors, personal hotspots, and network-connected rogues that pose real danger, taking policy-based action to trace, block, and locate the latter.


